Lets talk about a scenario here and take a look at manual way to find what we need with windbg + sos.
We will then see how we can automate this using Debug Analyzer.NET Analysis.
For learning pleasure and reuse, attached code snippet can be saved in snippets folder and used with Instant Analyzer feature too.
Scenario
An intranet ASP.NET application becomes very slow during off-peak hours. Since it's during off peak hours we can guess that it might not be due to heavy load.
There are several different tools and ways to troubleshoot this issue using profiling tools etc... But since running profiler etc might not be a great idea on production servers, we will use memory dumps to get the users who are using the application and then check what they are doing during that specific time of the issue.
(Maybe running a slow moving, large report?)
Let us see how this can be done in Windbg + SOS
[*** Dump all the objects of type System.Web.Security.FormsAuthenticationTicket ***]
0:034> !dumpheap -type System.Web.Security.FormsAuthenticationTicket
------------------------------
Heap 0
Address MT Size
10525a48 663b3f14 44
107f84f4 663b3f14 44
total 2 objects
------------------------------
Heap 1
Address MT Size
1454e4c0 663b3f14 44
145c0a00 663b3f14 44
14a04878 663b3f14 44
total 3 objects
------------------------------
Heap 2
Address MT Size
184fc27c 663b3f14 44
total 1 objects
------------------------------
Heap 3
Address MT Size
1c43ca44 663b3f14 44
1c511cfc 663b3f14 44
total 2 objects
------------------------------
total 8 objects
Statistics:
MT Count TotalSize Class Name
663b3f14 8 352 System.Web.Security.FormsAuthenticationTicket
Total 8 objects
[*** Let us dump out one of those objects ***]
0:034> !do 107f84f4
Name: System.Web.Security.FormsAuthenticationTicket
MethodTable: 663b3f14
EEClass: 663b3e50
Size: 44(0x2c) bytes
(C:\WINDOWS\assembly\GAC_32\System.Web\2.0.0.0__b03f5f7f11d50a3a\System.Web.dll)
Fields:
MT Field Offset Type VT Attr Value Name
79102290 4001e61 10 System.Int32 1 instance 2 _Version
790fd8c4 4001e62 4 System.String 0 instance 107f8520 _Name
7910c878 4001e63 18 System.DateTime 1 instance 107f850c _Expiration
7910c878 4001e64 20 System.DateTime 1 instance 107f8514 _IssueDate
7910be50 4001e65 14 System.Boolean 1 instance 0 _IsPersistent
790fd8c4 4001e66 8 System.String 0 instance 107f853c _UserData
790fd8c4 4001e67 c System.String 0 instance 107f8550 _CookiePath
[*** Now dumping out the field name called '_Name' ***]
0:034> !do 107f8520
Name: System.String
MethodTable: 790fd8c4
EEClass: 790fd824
Size: 28(0x1c) bytes
(C:\WINDOWS\assembly\GAC_32\mscorlib\2.0.0.0__b77a5c561934e089\mscorlib.dll)
String: USER1 <=== Heyaa!!! we got the user name!!!
Fields:
MT Field Offset Type VT Attr Value Name
79102290 4000096 4 System.Int32 1 instance 6 m_arrayLength
79102290 4000097 8 System.Int32 1 instance 5 m_stringLength
790ff328 4000098 c System.Char 1 instance 55 m_firstChar
790fd8c4 4000099 10 System.String 0 shared static Empty
>> Domain:Value 000f0050:790d884c 00114ca8:790d884c <<
7912dd40 400009a 14 System.Char[] 0 shared static WhitespaceChars
>> Domain:Value 000f0050:142d03f4 00114ca8:142d456c <<
Repeat the commands in line # 35 and 52 (8 times) for each object from the 1st command result.
Now lets see how this can be done in Debug Analyzer.NET (automation and reuse with 4 lines of code)
// Write a heading
WriteHeadLine("Forms Authentication Users");
//Get all objects of type 'System.Web.Security.FormsAuthenticationTicket'
IEnumerable<ClrObject> objs = Analyzer.CLR.GetClrObjectsByType("System.Web.Security.FormsAuthenticationTicket");
//Enumerate through all Objects of type 'System.Web.Security.FormsAuthenticationTicket'
foreach (ClrObject clrobj in objs)
{
ClrObject cobj = clrobj.ClrObjectFieldCollection["_Name"].ToClrObject();
WriteHtmlLine("User Name : {0}", cobj.ToString()); //Shows the string value using Extension Method
}
See the result below (all Disney characters on your intranet?)
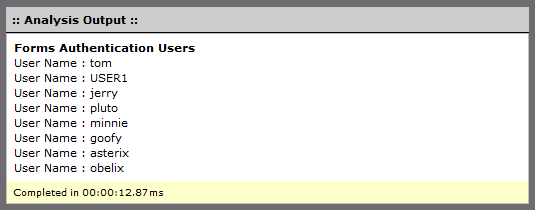
Tip: How many lines of code are needed to show the ClrObject in !do format?
Answer is 1 line of code!!! (write the following line of code, inside the foreach loop).
WriteHTMLLine(clrobj.ToHtml());
How cool is that? !!! 
(Use right-click and Save Target As...)
Download FormsAuthUsers.cs (850.00 bytes)